Encrypted VNC Connections with Stunnel
Stunnel has binary installers or stand alone executables for Windows and has a text configuration file. For Linux, Unix, or Mac platforms, you can build from source although you may prefer to use SSH tunneling (see Tunneling Using SSH, below).
Stunnel is free software released under the GNU GPL2 so there are no commercial restrictions for usage although there can be restrictions on the security algorithms for certain regions. See the stunnel license page for details.
Stunnel Operation
The VNC connection is configured so that instead of creating a direct unencrypted connection between the client and server, the client connects to a local stunnel instance. This stunnel then creates an encrypted connection to stunnel running on the system under test. The VNC connection is then tunneled through the encrypted connection and results in a further local connection on the server between the server stunnel and the VNC server.
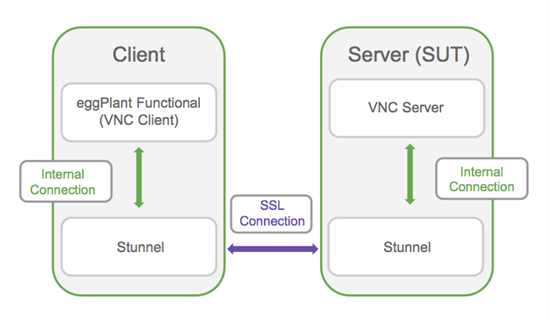
The client stunnel can be configured so the client can connect to multiple servers.
Step by Step: Setting up Stunnel
- Download the stunnel installer from www.stunnel.org
- Run the installer or extract the files from into a folder using a tool such as 7zip on the Eggplant Functional system. Also install or copy the stunnel files onto the SUT (or you can use a shared network folder).
The installation folder will contain an example stunnel.conf file.
- Edit the stunnel.conf file on the Eggplant Functional PC and add the lines:
[SUT1]
client = yes
accept = localhost:5801
connect = MY_SUT_HOST1:5901Replace MY_SUT_HOST1 with your SUT host or IP address. The local port, 5801, can be any free local port. The section name, e.g. [SUT1] only needs to be unique within the file. Repeat for each SUT e.g.
[SUT2]
client = yes
accept = localhost:5802
connect = MY_SUT_HOST2:5901 - Edit the stunnel.conf file on each SUT to add the lines:
[VNC]
accept = 5901
connect = 5900This assumes your VNC server is using the default port 5900.
- If running from a command window, run “tstunnel.exe” on each machine. It will automatically load the stunnel.conf in the same folder. If you have installed stunnel using the installer, there will be various startup options in the Windows Start Menu to start it as a GUI using stunnel.exe or as a service.
- Add Connection List entries for each SUT but pointing to the local address and port as in step 3. e.g.
SUT1, Host=localhost Port=5801
SUT2, Host=localhost Port=5802
The above configuration uses all the default settings for stunnel. There are numerous options for security and using your own certificates etc. See the stunnel documentation and various articles on the web.
Tunneling Using SSH
An alternate method for secure connection tunneling is to use SSH. This uses the same connection architecture as above but using SSH client and servers instead of stunnel.
SSH may be a more suitable approach when using MAC, Linux or Unix that normally includes an SSH client and server as standard.
On Windows, putty is a commonly used open source SSH client but the availability of SSH servers on Windows is more limited, particularly non-commercial options; hence stunnel being recommended for Windows.
An internet search for SSH tunneling will return numerous articles and guides.