VNCセキュリティ
この記事は、VNCの使用時にセキュリティを懸念している顧客が頻繁に尋ねる質問に多くの答えを提供します。VNCサーバを安全にするためにとることができるいくつかの異なる手順について説明します。
我々は、全国のDoDラボなどの安全な環境でVNCを使用している顧客を持っており、それらのケースではセキュリティの問題がすべての人々の満足のために対処されています。
VNCサーバを安全にデプロイすることは容易ですが、それがどのように行われるかは個々のネットワークインフラによります。最も重要なことは、VNCサーバのセキュリティはネットワークによって制御され、その逆ではないということを理解することです。もしVNCが動作しているマシンがネットワークファイアウォールの後ろにあり、VNCサーバが使用するポートがそのファイアウォールによって閉じられているならば、そのマシン上のVNCサーバはLAN上の他のものと同じくらい安全です。
VNCサーバのセキュリティ
VNCサーバ自体は、パスワードの使用とSSH暗号化を通じて、いくつかの方法で安全にすることができます。
パスワード
最初で最も明らかな方法は、パスワードで保護することで、パスワードを持つ者だけが接続を開始できます。二つ目の方法は、サーバが特定のIPアドレス(またはアドレス)または指定されたサブネット内のアドレスからの接続のみを受け入れるように設定できることです。
SSH暗号化
さらに一歩進めると、サーバはSSH(セキュアシェル)経由の接続のみを受け入れるように設定することができます。もしサーバがlocalhost(127.0.0.1)からの接続のみを受け入れるように設定されている場合、これはルーティングできないために偽装できません、サーバが受け入れる接続はSSHトンネル経由で作成された完全に安全な接続だけになります。
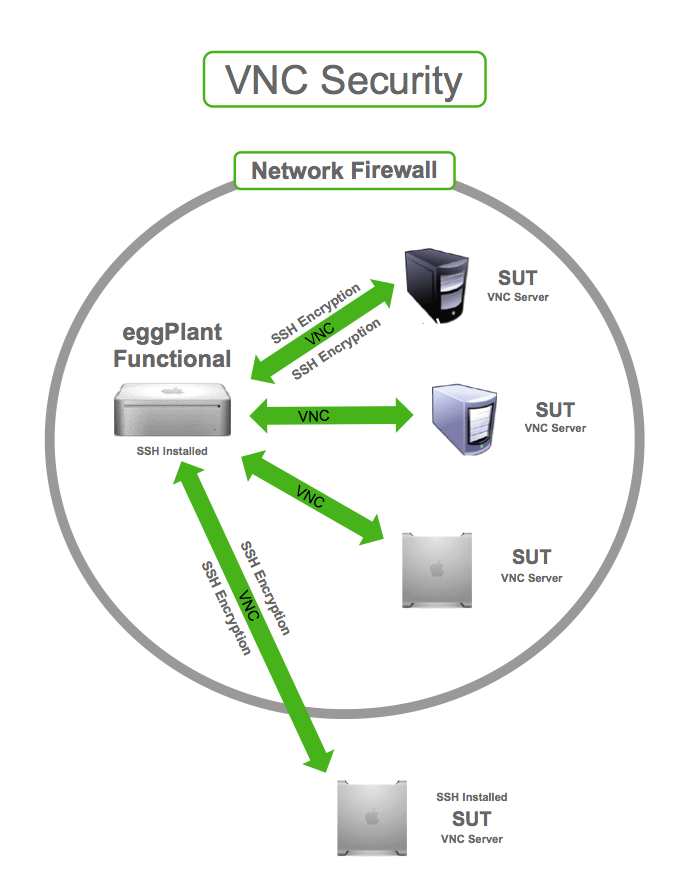 SSHを利用してVNCセキュリティを確保する
SSHを利用してVNCセキュリティを確保する
Eggplant FunctionalのConnection Listを通じてSSH接続を確立する方法については、Opening Secure Connectionsをご覧ください。
ネットワークセキュリティ
ネットワーク構成も、VNCサーバの外部で安全な方法で設定することができます:
仮想マシン
もう一つのアプローチ、そしてある意味では実装が簡単な方法は、Eggplant Functionalマシン上で仮想マシン(VM)を実行することです。Eggplant FunctionalマシンとVM(複数可)との間にNATtedネットワークを設定し、そのVM上でVNCサーバを実行してSUTとして機能させることができます。NATtedネットワークはEggplant Functionalマシンのファイアウォールの後ろにあり、VNCサーバは別のネットワーク上のコンピュータを模倣するプログラムの中で動作しています。その他のセキュリティ対策も、さらに安全なアプローチのためにVNCサーバの設定に適用することができます。
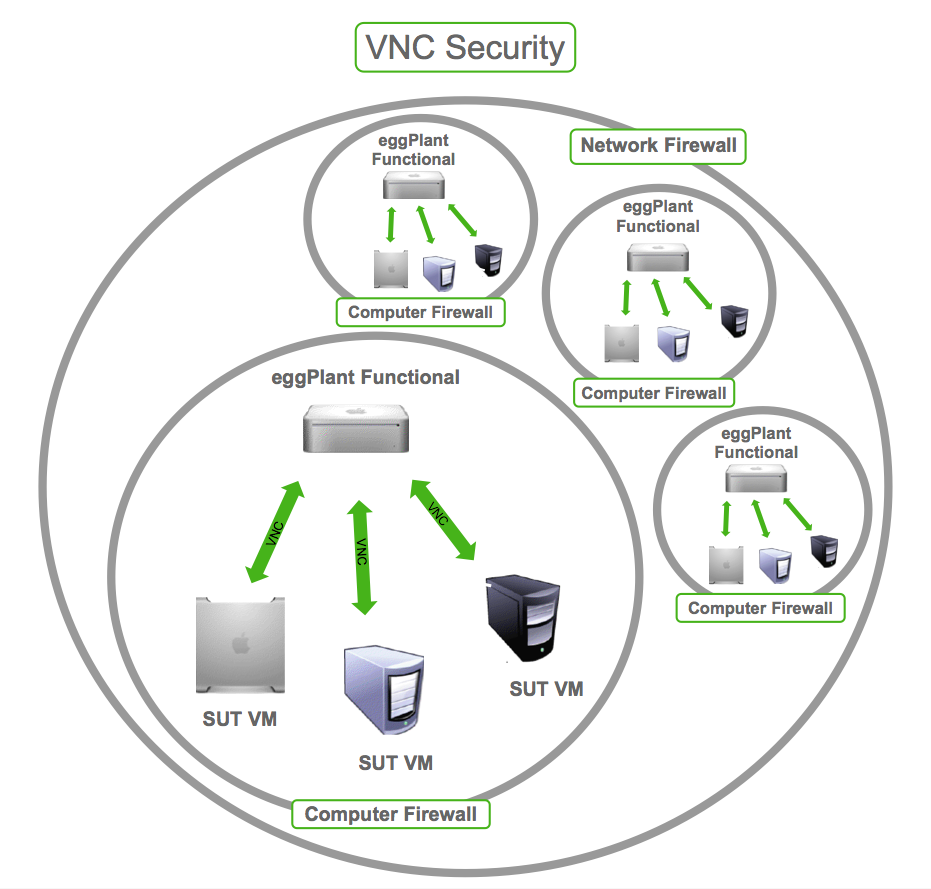 NATtedネットワークを使用してVNCセキュリティを確保する
NATtedネットワークを使用してVNCセキュリティを確保する
隔離
最後のアプローチは、テスト環境を外部接続のない独自のネットワークに置くことです。明らかにこれは、ウェブサーバなどの他のネットワークリソースへのアクセスを必要としないシナリオに対してのみ実行可能で、それが可能な場合には安全なテスト環境を実現します。最も基本的な形で、Eggplant Functionalテスト環境はお互いにネットワーク接続された2台のマシンにすぎません。