VNC Security
This article answers many frequently asked questions for customers who are concerned about security when using VNC connections in Eggplant Functional (EPF). It discusses some different steps that can be taken to make the VNC server secure.
We have customers using VNC in secure environments including DoD labs around the country, and in those cases the issues of security have been addressed to everyone’s satisfaction.
It is easy to deploy the VNC server securely, but how that is done is up to individual network infrastructure. The most important thing to understand is that the security of the VNC server is controlled by the network and not the other way around. If the machine that VNC is running on is behind a network firewall and the ports used by the VNC server are closed by that firewall, then the VNC server on that machine is as secure as anything else on the LAN.
VNC Server Security
The VNC server itself can be secured in a couple of ways; First by using a password, and second through SSH encryption.
Password
The first and most obvious is that it can be protected with a password, so that only those with the password can initiate a connection. The second is that the server can be set up to accept connections only from a specific IP address (or addresses) or addresses within a designated subnet.
SSH Encryption
Taking things a step further, the server can be configured to only accept connections via SSH (the secure shell). If the server is configured to accept connections only from localhost (127.0.0.1), which is unspoofable because it is not routable, the only connection the server will accept is one made via the SSH tunnel, thus creating a completely secure connection.
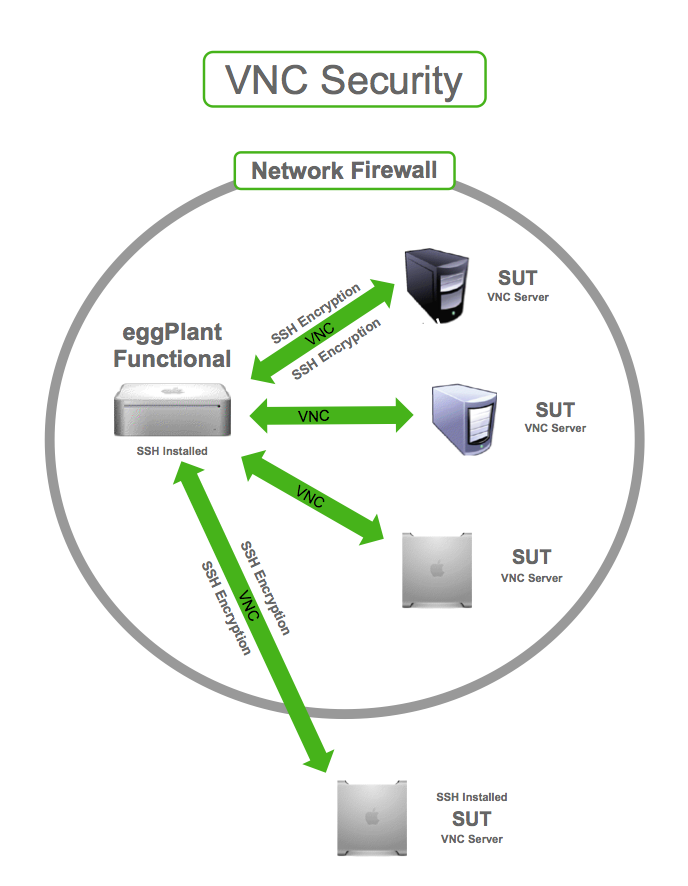
Using SSH to Ensure VNC Security
To read about making an SSH connection through the Connection List in Eggplant Functional, see Opening Secure Connections.
Network Security
The Network configuration can also be set up in a secure manner, outside of the VNC server:
Virtual Machines
Another approach, which is in some ways simpler to implement, is to run a virtual machine (VM) on the Eggplant Functional machine. A NATted network can be set up between the Eggplant Functional machine and the VM(s) and then the VNC server can be run on the VM to serve as the SUT. The NATted network is behind the firewall on the Eggplant Functional machine and the VNC server is running inside a program pretending to be a computer on a separate network. All the other security measures could be still be applied to configuring the VNC server for an even more secure approach.
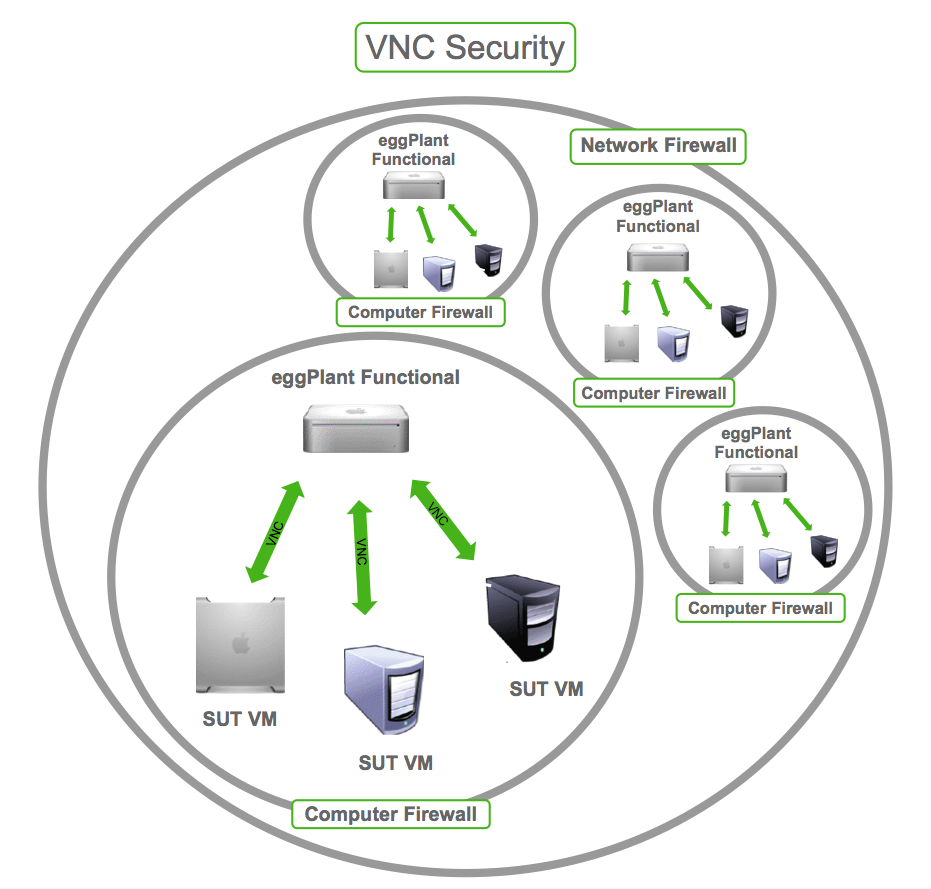
Using a NATted Network to Ensure VNC Security
Isolation
A final approach is to have the test environment on its own network with no external connections. Obviously this is only viable for scenarios that don’t require access to other network resources such as web servers, but when practicable it does produce a secure test environment. In its most basic form, an Eggplant Functional test environment is just two machines networked to each other.