Securing Your Installation
Securing your DAI installation involves configuring DAI settings as well as the environment where it runs. Considerations for each are provided in the following sections:
While threats to security are an ever-evolving challenge, this page provides considerations and information about methods you can use to help secure your DAI installation.
Deploying to a Secure Environment
Eggplant agents and processes require permission to launch system under test (SUT) connections, run tests, and capture file-based logs. We recommend you adhere to the principle of least privilege and avoid granting unnecessary permission, or a level of permission that is too permissive, for system users, network access, and file systems.
If you choose to install the DAI Run Agent as a Windows service, we strongly recommend that you use an appropriate user account with limited permissions, instead of the default Local System account.
For information about securing Eggplant Functional, which is a component of DAI, please see the Security Baseline Guidelines.
The security implemented in your company is also a layer of security for your DAI installation. Network firewalls, user access management, and operating system security features all help secure your company's systems. Following are some company security measures that also improve your DAI installation security.
Use a Firewall
Your company's firewalls provide security by restricting incoming and outgoing traffic on the network.
The DAI Server will need to be allowed through your firewall. See Be Aware of Port Usage below for more information.
Control User Access
Your company IT department secures the network and systems, including the machines where you will install and run DAI, by managing user access. DAI also provides user account management and controls access to its assets using roles. See DAI's Built-In User and Access Management for more information. If your company uses an identity provider for user account management, such as Microsoft Entra ID, you can integrate it with DAI. While the purpose of this integration is to enable single sign-on (SSO) authentication for the convenience of DAI users, it also centralizes user account management in the identity provider. See Enable SSO in DAI below for more information about this integration.
Encrypt the Drive Where DAI Is Installed
If your DAI installation is an on-premises ("on-prem") Windows installation, consider encrypting the hard drive of the system where you plan to install DAI. This prevents anyone who does not have the appropriate key or password from accessing the drive.
Configuring DAI for Optimal Security
The following topics describe ways to configure DAI for improved security in your installation.
Upgrade to the Latest DAI Version
Keeping your DAI installation at the latest version ensures you have the latest security updates available in DAI. See the DAI Downloads page for the latest version available. You can find a list of updates in the Release Notes for each release.
Install the DAI Server on a Separate System
For Windows on-premises installations, we recommend installing the DAI Server on a separate system from the DAI agents, Eggplant Functional, and other non-Eggplant applications. This is to minimize the risk of horizontal privilege escalation, which is limiting a malicious user who gains access to one part of the system from accessing and compromising the rest of the system.
Choose Secure Installation and Configuration Options
The following security-related configuration options require you to perform an Advanced installation, or modify your DAI configuration after installation. Because setting these options can impact DAI operation, please contact our Customer Support with any questions or for assistance.
Beginning with 25.3, DAI Windows on-prem installations store internal process credentials in the Windows operating system Credential Manager (Locker). Previous versions stored them in the DAI configuration file.
For DAI container deployments with Kubernetes, DAI has always stored credentials in the Kubernetes secret manager.
| Security Option | Description |
|---|---|
| Configure DAI to Use HTTPS with SSL | For Windows on-premises installations: You should configure DAI to use HTTPS with Secure Sockets Layer (SSL) internet security protocol during installation by running an "Advanced Install". Configuring DAI to use HTTPS requires a trusted certificate and a PEM format SSL key. See Run an Advanced Install and Add Settings for Self-Signed SSL Secure Certificates for more information. |
| Configure DAI Containers to use TLS certificates | For Container deployments: Using TLS certificates is mandatory. You should configure DAI to use Transport Layer Security (TLS) as described in Configuring TLS. |
| Encrypt the DAI Message Broker Communications | DAI embeds the RabbitMQ message broker to handle communications among its components. You can configure DAI to encrypt these communications by specifying variables in the DAI configuration file. See Encrypt RabbitMQ Communications for more information. |
| Secure the DAI SMTP Server Connection | Because the SMTP server is likely to be on a different machine from your DAI Server, you should configure DAI to use a secure connection to your SMTP server. See SMTP Settings for options. |
Be Aware of Port Usage
DAI uses a number of ports as part of its operation. Only the DAI Server port (8000) needs to be allowed through your company firewall. The majority of the ports DAI uses are for internal communication among its processes and services within the same network. The following table describes the different types of port usage:
| Port Usage | Description |
|---|---|
| DAI Default Port | By default, the DAI installation on Windows assigns port 8000 to its server. This is the only one that needs to be allowed access through your company firewall. You can change it by following the instructions in Change the Eggplant DAI Port on Windows. DAI also uses several other ports internally by default, which you can see in Default Port Usage on the DAI Prerequisites page. You can change these default ports, if necessary. Instructions are provided in the Change the Eggplant DAI Port on Windows section on the Post-Installation Configuration page. |
| Eggplant Functional Connection Port | The DAI Design and Run Agents communicate with Eggplant Functional (EPF), which is the component that runs the tests script. Eggplant listens for commands from DAI on the EGGDRIVE_PORT, which you configure in the Agent command line arguments. |
| System Under Test (SUT) Connection Default Ports | DAI can connect to remote SUTs to run tests. Some SUT connection types require a port and have a default port. For more information about default SUT ports, see Default Ports for SUT Connections on the DAI Prerequisites page. For information about specifying a SUT port when you create a connection, see Managing SUTs in DAI. |
Enable Single Sign-On (SSO) in DAI
DAI provides built-in user and access management as described below in Use DAI's Built-In User and Access Management. But if your company uses a network identity provider, such as Entra ID, you can also integrate with it to enable SSO capability in DAI. See Use Your Company's Network Identity Provider for information about how enabling SSO can increase security in DAI.
Manage Users and Access in DAI
Use DAI's Built-In User and Access Management
DAI provides built-in user and access management (with an embedded identity and access management product: "Keycloak.") For information about managing users, access groups, and membership in those groups in DAI, see About Eggplant Roles and Add a New User.
For information about managing user access in DAI, see Limiting User Access with DAI Roles below.
Use Your Company's Network Identity Provider
If your company uses a network identity provider to manage users, such as Entra ID, you have the option to integrate that identity provider with DAI and its built-in user management. With this integration, the identity provider manages user data, and DAI continues to own and manage the DAI access groups and membership in those groups.
The main advantage of integrating DAI with an identity provider is the convenience of single sign-on (SSO) capability for your DAI users. However, it also simplifies user account management (the provisioning and de-provisioning of users) by using the identity provider that is managed by your IT department. For more information about enabling SSO in DAI, see Integrating Single Sign-On (SSO) Authentication in DAI.
Limit User Access with DAI Roles
To control user access to DAI assets (models, test cases, APIs, licenses, and so on), DAI provides 3 roles that you can assign to users: Viewer, User, and Admin, with the Admin role having administrator privileges to perform tasks. See About Eggplant Roles for information about the different roles and what privileges each has.
You should limit the number users who are assigned the DAI Admin role to limit the number of users who have administrative privileges in DAI.
Also note, that in DAI 7.5 (with Keycloak version 26), Keycloak creates a temporary Admin user. You will see the following warning at the top of the Keycloak Admin Console when you log in with this temporary user:
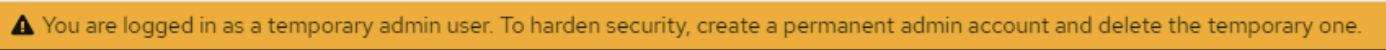 DAI Keycloak Temporary User Warning
DAI Keycloak Temporary User Warning
You should only use this temporary user until you can create a more secure, permanent administrator user. See Admin bootstrap and recovery in the Keycloak documentation for more information.
Secure Access to Your Test Assets
The following table provides a few things you can do to secure your DAI test assets:
| Option | Description |
|---|---|
| Restrict access to your installation location | For Windows on-premises installations: restrict user access to the DAI installation directory: C:\ProgramData\Eggplant\Digital Automation Intelligence\, which includes the DAI configuration file (config.yml), and its subdirectories. |
| DAI PostgreSQL database | DAI stores its data, including information about models, tests, and licenses, in a PostgreSQL database. The columns in the database that contain sensitive data are encrypted. For added security in a Windows on-premises installation: consider encrypting the entire drive where DAI is installed as described above in Encrypt the Drive Where DAI is Installed. For container deployments: create a secret with credentials as described in the PostgreSQL section of the Deploying Eggplant DAI in Containers |
| Safely store your test suites | DAI provides two options for securing your test suites: - DAI internal storage. For more information about DAI internal storage, see Manage Suites (Internal Storage)(DAI Design Agent). - Integration with Git repositories. For more information about the Git integration, see Working with Repositories in DAI. |